January’s big security news was the Mother of All Breaches, the release of a massive database containing 26 billion records built from previous breaches across numerous websites, including Adobe, Dropbox, LinkedIn, and Twitter. It’s unclear how much of the leaked data is new, but it’s a good reminder to update your passwords for accounts on compromised sites, especially those you reused on another site. Cybernews has a leak checker that reports which breached sites include your data.
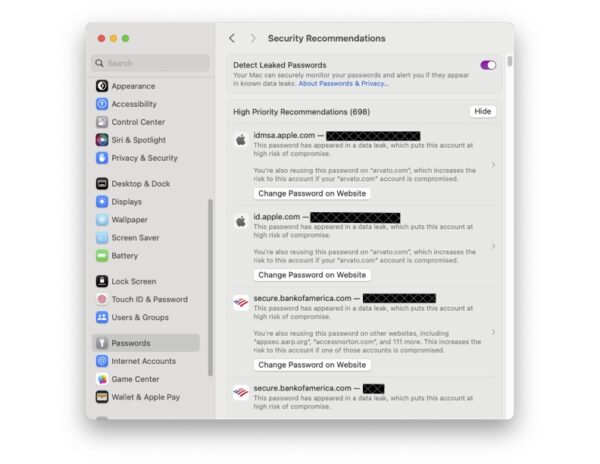
Apple also has a tool for you that can help. Now that Passwords is one of the system settings on your Mac or iOS device you can click on “Security Recommendations” and the Password AutoFill passwords list in iOS, iPadOS, and macOS indicate which of a your saved passwords will be reused with other websites, passwords that are considered weak, and passwords that have been compromised by a data leak.
-
Passwords are marked reused if the same password is seen used for more than one saved password across different domains.
- Passwords are marked weak if they may be easily guessed by an attacker. iOS, iPadOS, and macOS detect common patterns used to create memorable passwords, such as using words found in a dictionary, common character substitutions (such as using “p4ssw0rd” instead of “password”), patterns found on a keyboard (such as “q12we34r” from a QWERTY keyboard), or repeated sequences (such as “123123”). These patterns are often used to create passwords that satisfy minimum password requirements for services, but are also commonly used by attackers attempting to obtain a password using brute force.Because many services specifically require a four- or six-digit PIN code, these short passcodes are evaluated with different rules. PIN codes are considered weak if they are one of the most common PIN codes, if they are an increasing or decreasing sequence such as “1234” or “8765,” or if they follow a repetition pattern, such as “123123” or “123321.”
- Passwords are marked leaked if the Password Monitoring feature can claim they have been present in a data leak.
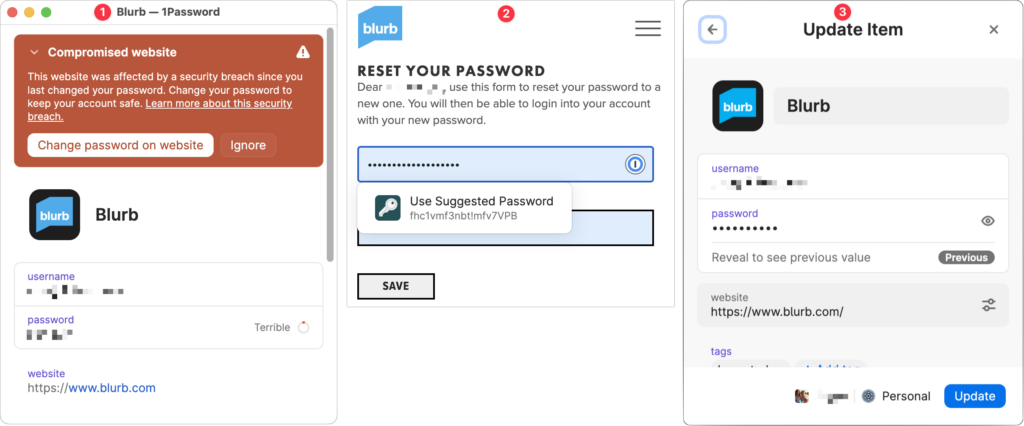
More generally, password managers often have a feature that checks your passwords against the Have I Been Pwned database of breaches and helps you change compromised passwords—1Password’s is called Watchtower, shown below.You can also search Have I Been Pwned directly. Don’t panic if your email address appears in numerous breaches because some of the theoretically compromised accounts may be defunct sites, trivial sites you used once 10 years ago, or duplicate password manager entries for a site whose password you already updated.
(Featured image by iStock.com/Prae_Studio)

