Audit Your Trusted Device Lists for Greater Security
One of the ways companies protect critical account information is by remembering the devices you use to log in as “trusted devices” or “authorized devices.” Those logins will usually have been protected by two-factor authentication or another mechanism that guarantees the device is being used by you, its owner. Subsequent logins from those devices may be more convenient for you due to requiring only a username and password, and trusted devices may automatically receive two-factor authentication codes. That’s how Apple ensures you are who you say you are when you log in to your Apple ID on a previously unseen device.
Although trusted devices can help increase your security, they can also reduce it. If an attacker were to gain access to one of your trusted devices, they would have a better chance of breaking into your accounts or masquerading as you when setting up new accounts. As a result, it’s important to audit your trusted devices occasionally and make sure you still control all of them. The first time you do this, you may be shocked to see that a Mac you last used years ago could still be receiving Apple ID verification codes. Removing unused trusted devices from an account makes it more secure with no downside.
We can’t provide a comprehensive list of services that track trusted devices, but many of you use two high-profile ones: Apple and Google. In addition, most password managers with online accounts also rely on trusted devices—we’ll look at 1Password here, but if you use another password manager, look through its settings to see if it maintains a list of trusted devices.
Remove Trusted Apple Devices
Apple gives you access to the list of all your current Apple devices in System Settings > Your Name on the Mac and in Settings > Your Name on the iPhone and iPad. (You can also log in to appleid.apple.com, click Sign-in and Security in the sidebar, and click Account Security.) Some of the devices shown may not be trusted devices—there isn’t much to worry about with a HomePod, and some old Macs may not be logged in. Click or tap any device to learn more about it—the 27-inch iMac in the screenshot below is trusted and can receive Apple ID verification codes.
Unfortunately, Apple doesn’t display the date the device was last used, which can help identify ancient devices. So look for any devices that you don’t immediately recognize as being in use—particularly Macs, iPhones, and iPads—and remove them from your account. Don’t worry about inadvertently removing a device you do use—at worst, you’ll have to log in to your Apple ID again the next time you use it.

Remove Trusted Google Devices
You can quickly load Google’s list of trusted devices by logging in to your Google account at myaccount.google.com/device-activity. To navigate there manually, go to your Google Account at myaccount.google.com, click Security in the sidebar, scroll down to find the Your Devices tile, and click Manage All Devices. Google says it keeps track of sessions (whenever you sign in) on trusted devices for only 28 days, but the sessions shown on “unknown device(s)” below are far older than that. Google helps by displaying the location and date of most sessions.
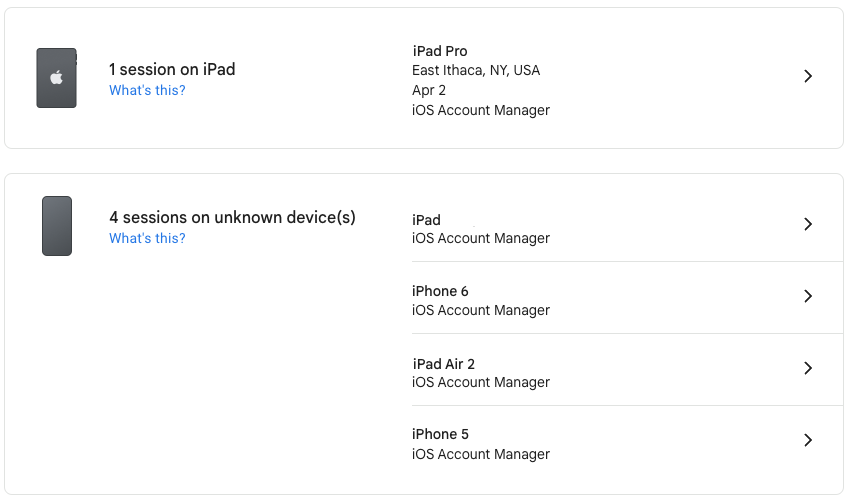
Click a session to learn more about it, including the date you first signed in on that device. For devices you no longer use, click Sign Out to remove access to your Google Account.

Remove Trusted 1Password Devices
To remove old trusted devices from 1Password, start by logging in to 1Password.com, clicking your name at the top right, and choosing My Profile—you can also navigate directly to my.1password.com/profile. As you can see, 1Password provides information about each trusted device and browser, showing its IP address, location, operating system version, and last access time.
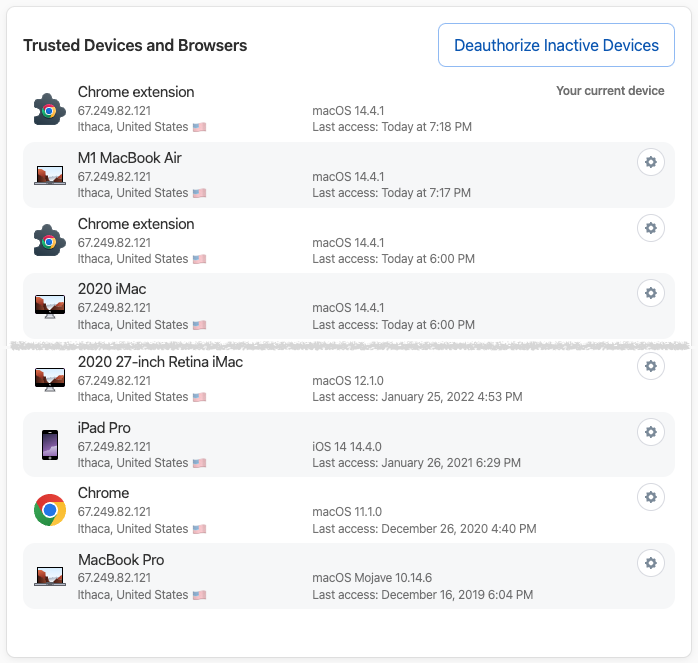
It’s easiest to click Deauthorize Inactive Devices, at which point 1Password will ask if you want to deauthorize all devices that haven’t been used in the last 60 days. If you prefer a more targeted approach, click the gear next to a device or browser you want to remove and click Deauthorize Device in the dialog that appears.

Again, the only harm that could come from deauthorizing a device you still use is that you will have to log in to 1Password again.
After you’ve audited your Apple, Google, and password-manager trusted devices—and any other accounts you may have that maintain such lists—there’s no need to check again right away. Once a month or once a quarter would be sufficient for most people.
That said, if you ever notice any unusual account activity, look at your trusted device lists to ensure you recognize everything. If there’s a device you don’t recognize or one that was used at an unfamiliar place or at a time when you were otherwise occupied, immediately remove it and change that service’s password.
(Featured image by iStock.com/Ildo Frazao)
Social Media: We all accumulate “trusted devices” in our Apple, Google, and password manager accounts, but it’s important to remove devices you no longer use because they could be security risks.




